Imagine a world where data breaches are relics of the past, where sensitive information remains untouchable by malicious actors. This isn’t science fiction; it’s the promise of blockchain technology applied to data security. Blockchain’s decentralized, immutable ledger offers a revolutionary approach to protecting our digital assets, creating a fortress of security against the ever-evolving threats of the modern digital landscape.
This exploration delves into the heart of this transformative technology, unveiling its potential to reshape the future of data protection.
From its fundamental principles to its real-world applications across diverse industries, we’ll unravel the intricate mechanisms that make blockchain a game-changer in data security. We’ll examine how its unique properties address the critical challenges of data integrity, access control, and privacy, providing concrete examples and insightful comparisons to traditional methods. Prepare to be captivated by the power and potential of blockchain to safeguard our digital world.
Introduction to Blockchain and Data Security
Blockchain technology, at its core, is a revolutionary system for recording and verifying data. Imagine a digital ledger, not stored in a single location but distributed across a vast network of computers. This decentralized nature is the key to its strength in data security. Each “block” in the chain contains a batch of validated transactions, cryptographically linked to the previous block, creating an immutable and transparent record.
Altering even a single piece of data would require altering every subsequent block, a computationally infeasible task given the sheer scale and distributed nature of the network. This inherent immutability is what makes blockchain so compelling for securing data.Blockchain’s decentralized architecture is its greatest security asset. Unlike traditional databases held by a single entity, which are vulnerable to hacking and single points of failure, blockchain data is distributed across many nodes.
Compromising one node does not compromise the entire system. This redundancy drastically reduces the risk of data breaches and ensures data integrity even in the face of malicious attacks. The consensus mechanisms employed by various blockchain networks, such as Proof-of-Work or Proof-of-Stake, further enhance security by requiring agreement from a significant portion of the network before any new block is added to the chain.
This prevents fraudulent transactions and ensures data accuracy.
Blockchain’s Mitigation of Data Breaches
The 2017 Equifax data breach, exposing the personal information of nearly 150 million people, highlighted the vulnerability of centralized databases. Had Equifax utilized a blockchain-based system, the impact could have been significantly lessened. The sensitive data, instead of residing in a single, vulnerable database, would have been distributed across a network. Even if one node were compromised, the integrity of the remaining data would remain intact.
Moreover, the immutable nature of the blockchain would have made it nearly impossible for attackers to alter or delete records after the breach. Similarly, the 2014 Sony Pictures hack, which resulted in the release of sensitive emails and corporate data, could have been mitigated by using a blockchain system to manage and secure sensitive information. The decentralized and immutable nature of blockchain would have made it significantly more difficult for hackers to access and manipulate the data.
The use of cryptographic techniques would have added another layer of protection, encrypting sensitive data and making it virtually unreadable without the correct decryption keys.
Blockchain’s Role in Data Integrity and Immutability
Blockchain technology revolutionizes data security by introducing a novel approach to data management, fundamentally altering how we perceive and protect information. Its core strength lies in its ability to ensure data integrity and immutability, offering a level of security unattainable with traditional methods. This inherent trustworthiness stems from the decentralized and cryptographically secured nature of the blockchain.Blockchain ensures data integrity through its unique architecture.
Each block in the chain contains a cryptographic hash of the previous block, creating an unbreakable chain of records. Any attempt to alter data in a previous block would change its hash, instantly making the alteration detectable and invalidating the entire chain following the manipulated block. This inherent self-auditing mechanism is the foundation of blockchain’s immutability.
Immutability and Data Security
Immutability, the inability to alter or delete data once it’s recorded on the blockchain, is a cornerstone of its security. This characteristic prevents unauthorized modifications, data tampering, and fraudulent activities. The cryptographic hashing and chain structure ensure that any change, no matter how subtle, is immediately apparent, maintaining the integrity and authenticity of the data throughout its lifecycle. This stands in stark contrast to traditional databases, where data can be easily altered or deleted, potentially compromising its reliability and trustworthiness.
Blockchain’s Mechanisms for Data Integrity
Blockchain utilizes several mechanisms to guarantee data integrity. Cryptographic hashing ensures that even a minor change to the data results in a completely different hash value. This makes tampering immediately evident. The distributed ledger nature of blockchain further enhances security. Multiple copies of the blockchain exist across a network of nodes, making it incredibly difficult for a single entity to manipulate the data.
Consensus mechanisms, such as Proof-of-Work or Proof-of-Stake, further ensure the integrity of the blockchain by requiring agreement from a majority of nodes before any new block is added.
Real-World Examples of Blockchain’s Effectiveness
The application of blockchain for data integrity is rapidly expanding. In the supply chain management industry, blockchain is used to track products from origin to consumer, ensuring authenticity and preventing counterfeiting. For example, companies like Walmart are using blockchain to trace the origin of their food products, providing consumers with greater transparency and confidence in the safety and quality of their food.
Similarly, in the healthcare industry, blockchain is being explored to secure patient medical records, ensuring data integrity and privacy. This prevents unauthorized access and ensures that patient information remains accurate and reliable. The diamond industry also leverages blockchain to track diamonds from mine to market, verifying their authenticity and ethical sourcing.
Comparison of Traditional Databases and Blockchain Databases
The following table highlights the key differences between traditional databases and blockchain databases concerning data integrity:
| Feature | Traditional Database | Blockchain Database |
|---|---|---|
| Data Mutability | Mutable (data can be easily altered or deleted) | Immutable (data cannot be altered or deleted after recording) |
| Data Integrity | Relies on access controls and auditing mechanisms, which can be vulnerable | Ensured by cryptographic hashing and distributed consensus mechanisms |
| Transparency | Limited transparency, data access is often controlled | High transparency, all transactions are recorded and publicly verifiable (depending on the blockchain’s design) |
| Security | Susceptible to data breaches and unauthorized modifications | Highly secure due to cryptographic hashing, distributed ledger, and consensus mechanisms |
Blockchain for Data Access Control and Authorization
Blockchain technology, with its inherent security and transparency, offers a revolutionary approach to managing data access control and authorization. Traditional centralized systems often suffer from single points of failure and vulnerability to unauthorized access. Blockchain, however, distributes control and enhances auditability, leading to a more robust and secure system for managing sensitive data. This section explores the design of such a system, compares different permissioning models, and addresses potential vulnerabilities and their mitigation.
A blockchain-based access control system leverages the immutability and cryptographic security of the blockchain to define and enforce access rules. Instead of relying on a central authority to manage permissions, access rights are encoded as transactions on the blockchain, making them transparent, auditable, and resistant to tampering. This distributed ledger approach significantly reduces the risk of unauthorized access or modification of access controls.
Blockchain-Based Access Control System Design
A system could be designed where each data asset is represented by a unique token on the blockchain. Access permissions are then granted by issuing specific smart contracts that govern the conditions under which a user or application can interact with the data asset. These smart contracts could define granular access controls, such as read-only access, write access, or execute access.
The blockchain would record all permission grants, revocations, and access attempts, creating a complete and immutable audit trail. For instance, a healthcare provider could use this system to manage access to patient medical records, ensuring only authorized personnel can view or modify the data. Each access event would be recorded on the blockchain, providing a verifiable record of who accessed what and when.
This would greatly improve compliance and accountability.
Comparison of Permissioning Models
Several permissioning models exist for blockchain networks, each influencing how access control is managed. Permissioned blockchains, such as Hyperledger Fabric, offer fine-grained control over who can participate in the network and what actions they can perform. This allows for a more controlled and secure environment for managing sensitive data. In contrast, permissionless blockchains, like Bitcoin or Ethereum, have open participation, making them less suitable for applications requiring strict access control.
Hybrid models also exist, offering a balance between permissioned and permissionless characteristics. The choice of permissioning model depends on the specific requirements of the application and the desired level of security and control. For example, a financial institution managing sensitive customer data might opt for a permissioned blockchain to maintain strict control over access.
Potential Vulnerabilities and Mitigation Strategies
While blockchain offers significant advantages, blockchain-based access control systems are not immune to vulnerabilities. One potential vulnerability is the risk of compromised private keys. If a user’s private key is compromised, an attacker could potentially gain unauthorized access to the data. Mitigation strategies include using multi-signature wallets, hardware security modules (HSMs), and implementing robust key management practices.
Another vulnerability is the potential for smart contract vulnerabilities. Faulty smart contracts could allow attackers to bypass access controls. Thorough auditing and testing of smart contracts are crucial to mitigate this risk. Finally, the blockchain network itself could be susceptible to attacks, such as 51% attacks. Choosing a robust and well-established blockchain network with a high level of decentralization and security is essential.
Regular security audits and updates are also crucial to maintain the security and integrity of the system.
Blockchain in Data Privacy and Confidentiality
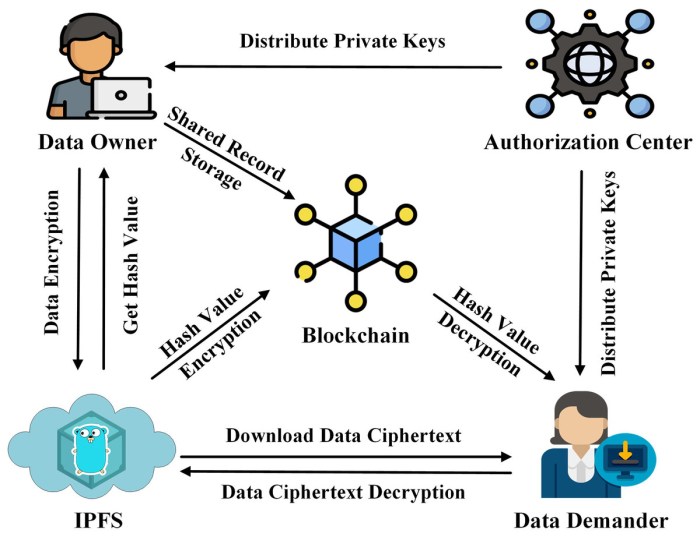
Blockchain technology, with its inherent cryptographic features and decentralized architecture, offers a compelling approach to enhancing data privacy and confidentiality. Unlike traditional centralized databases vulnerable to single points of failure and data breaches, blockchain distributes data across a network, making it significantly more resilient and secure. This inherent security, coupled with advanced cryptographic techniques, allows for unprecedented levels of control over sensitive information.The robust security of blockchain stems from its foundation in cryptography.
Every transaction is cryptographically secured, ensuring data integrity and preventing unauthorized modifications. This foundational layer of security forms the bedrock upon which more sophisticated privacy-enhancing mechanisms can be built.
Cryptography for Data Confidentiality
Blockchain utilizes various cryptographic techniques to ensure data confidentiality. Symmetric-key encryption, where the same key is used for both encryption and decryption, can protect data at rest and in transit. Asymmetric-key cryptography, employing separate public and private keys, enables secure communication and authentication. Digital signatures, generated using private keys, verify the authenticity and integrity of data, preventing tampering and ensuring non-repudiation.
For instance, a healthcare provider could encrypt patient medical records using a symmetric key, and then encrypt that key using the patient’s public key, ensuring only the patient can access their records.
Zero-Knowledge Proofs for Enhanced Privacy
Zero-knowledge proofs (ZKPs) represent a significant advancement in blockchain’s privacy capabilities. ZKPs allow individuals to prove the validity of a statement without revealing any underlying information. For example, a user could prove they are over 18 years old without disclosing their exact age. In a blockchain context, ZKPs can be used to verify identity or access rights without exposing sensitive personal data.
This is particularly useful in scenarios requiring stringent data privacy, such as verifying eligibility for a government benefit program without divulging personal details. Imagine a system where individuals can prove their vaccination status without revealing their medical history. This is a powerful application of ZKPs within a blockchain framework.
Blockchain Protecting Sensitive Personal Data
Several real-world applications showcase blockchain’s potential for safeguarding sensitive data. Consider the use of blockchain in managing personal medical records. Patients could maintain complete control over their data, granting access only to authorized healthcare providers. Each access attempt would be recorded on the immutable blockchain ledger, creating an auditable trail. Similarly, blockchain can enhance data privacy in supply chain management.
Tracking sensitive product information, such as origin and handling, across the supply chain ensures transparency and accountability, while simultaneously protecting confidential business information. Furthermore, blockchain-based digital identity systems offer individuals more control over their personal data, allowing them to selectively share information with different organizations.
Advantages and Disadvantages of Blockchain for Data Privacy
The use of blockchain for data privacy offers significant advantages, but also presents certain challenges. It’s crucial to weigh these factors carefully before implementing blockchain solutions.
The following points highlight the advantages and disadvantages:
- Advantages: Enhanced data security through cryptographic techniques and decentralized architecture; increased transparency and auditability; improved data control for individuals; reduced reliance on centralized authorities.
- Disadvantages: Scalability limitations for large datasets; potential for high energy consumption depending on the consensus mechanism; complexity of implementation and integration; the need for specialized technical expertise.
Scalability and Performance of Blockchain in Data Security Applications
Blockchain technology, while revolutionary in its approach to data security, faces significant hurdles when applied to large-scale deployments. The inherent limitations in transaction processing speed and storage capacity present challenges that must be addressed for blockchain to become a truly ubiquitous solution for data security in diverse applications. This section explores these scalability challenges, examines various consensus mechanisms and their performance implications, and Artikels strategies for enhancing blockchain’s capabilities in this critical area.The inherent limitations of blockchain technology, particularly in processing speed and storage capacity, pose significant challenges when scaling up to handle the demands of large-scale data security applications.
Traditional blockchains, reliant on a consensus mechanism involving all network participants, struggle to maintain efficiency as the number of transactions and nodes increases. This leads to slower transaction times, increased latency, and higher costs, hindering its practicality for applications requiring high throughput and low latency. The trade-off between security and speed becomes increasingly critical as the scale of the application grows.
Scalability Challenges in Blockchain Data Security
The limitations of blockchain technology in handling a high volume of transactions are a primary concern for its adoption in large-scale data security applications. The process of validating and adding transactions to the blockchain becomes increasingly slow and resource-intensive as the number of transactions grows. This can lead to significant delays in processing sensitive data, rendering the system impractical for time-sensitive applications such as real-time financial transactions or critical infrastructure monitoring.
Furthermore, the storage requirements for the blockchain itself grow linearly with the number of transactions, posing challenges for maintaining a distributed ledger across numerous nodes. The cost of maintaining and operating a large-scale blockchain network can also be prohibitive, limiting its accessibility to smaller organizations. For example, a global supply chain management system relying on blockchain to track goods would require extremely high transaction throughput and efficient data management to remain viable.
Comparison of Consensus Mechanisms and Performance
Different consensus mechanisms play a crucial role in determining the scalability and performance of a blockchain system. Proof-of-Work (PoW), commonly used in Bitcoin, is known for its security but suffers from low transaction throughput due to its energy-intensive mining process. Proof-of-Stake (PoS), on the other hand, offers improved scalability by reducing energy consumption and increasing transaction speed. However, PoS can be vulnerable to attacks if not implemented carefully.
Other mechanisms like Delegated Proof-of-Stake (DPoS) and Practical Byzantine Fault Tolerance (PBFT) offer different trade-offs between security, scalability, and energy efficiency. The choice of consensus mechanism significantly impacts the overall performance and suitability of the blockchain for specific data security applications. For instance, a system requiring high throughput, like a decentralized identity management platform, might benefit from a faster consensus mechanism like DPoS, while a system prioritizing security above all else might opt for a more robust, albeit slower, mechanism like PoW.
Strategies for Improving Blockchain Scalability and Performance
Several strategies can be employed to enhance the scalability and performance of blockchain in data security applications. These include sharding, which partitions the blockchain into smaller, more manageable pieces, allowing for parallel processing of transactions. Layer-2 scaling solutions, such as state channels and sidechains, process transactions off-chain before committing them to the main blockchain, significantly increasing throughput. Furthermore, optimizing the blockchain architecture, improving data compression techniques, and employing more efficient consensus mechanisms can all contribute to better performance.
The use of specialized hardware and optimized software can further enhance transaction processing speeds and reduce latency. For example, companies like Ethereum are actively developing and implementing sharding to improve the scalability of their network, allowing for a significant increase in transaction throughput and reducing the load on individual nodes.
Real-World Applications of Blockchain in Data Security

Blockchain technology, with its inherent security features, is rapidly transforming various industries by enhancing data integrity, privacy, and access control. Its decentralized and immutable nature offers a compelling alternative to traditional centralized systems, particularly in sectors grappling with sensitive data and complex trust relationships. The following examples illustrate the practical applications and associated benefits and challenges.
Blockchain in Healthcare Data Management
The healthcare industry deals with highly sensitive patient data, making security paramount. Blockchain offers a solution for secure and transparent data sharing among healthcare providers, patients, and insurance companies. Imagine a system where patient medical records are stored on a blockchain, allowing authorized individuals access while maintaining patient privacy and control. This eliminates the risk of data breaches and ensures data integrity.
However, challenges include integrating blockchain with existing healthcare systems, addressing scalability issues for large datasets, and establishing regulatory compliance.
Blockchain in Financial Transactions and Identity Verification
The financial sector is another prime beneficiary of blockchain’s security capabilities. Blockchain technology can revolutionize payment systems by enabling faster, more secure, and transparent transactions. Cryptocurrencies like Bitcoin exemplify this, but the applications extend to other areas, such as identity verification and Know Your Customer (KYC) compliance. By storing identity data on a blockchain, financial institutions can verify identities more efficiently and securely, reducing fraud and improving compliance.
Challenges here include the need for interoperability between different blockchain networks and the potential for regulatory uncertainty.
Blockchain in Supply Chain Management and Tracking
Supply chain management often involves multiple stakeholders and complex logistics, creating vulnerabilities for counterfeiting and fraud. Blockchain can enhance transparency and traceability by recording every step of a product’s journey on an immutable ledger. This enables businesses to verify the authenticity of products, track their origin, and improve overall supply chain efficiency. For example, a luxury goods manufacturer could use blockchain to track its products from production to retail, ensuring authenticity and preventing counterfeiting.
However, implementing blockchain across complex global supply chains requires significant technological investment and coordination among different stakeholders.
| Industry | Use Case | Benefits | Challenges |
|---|---|---|---|
| Healthcare | Secure Patient Record Management | Enhanced data privacy, improved data integrity, efficient data sharing | System integration, scalability, regulatory compliance |
| Finance | Secure Transactions & Identity Verification | Faster, more secure transactions, reduced fraud, improved KYC compliance | Interoperability, regulatory uncertainty |
| Supply Chain | Product Tracking & Authenticity Verification | Increased transparency, improved traceability, reduced counterfeiting | Technological investment, stakeholder coordination |
Future Trends and Challenges in Blockchain Data Security
The future of blockchain in data security is a dynamic landscape shaped by both exciting advancements and significant hurdles. While blockchain’s inherent security features offer a compelling solution to many data vulnerabilities, its widespread adoption hinges on overcoming several key challenges. The coming years will witness a confluence of technological innovation and regulatory adaptation, ultimately determining blockchain’s impact on the future of secure data management.Emerging technologies are poised to significantly enhance blockchain’s security capabilities.
The integration of these advancements will not only improve existing functionalities but also unlock entirely new applications in data security. Simultaneously, obstacles related to scalability, interoperability, and regulatory uncertainty need careful consideration and proactive solutions to ensure blockchain’s potential is fully realized.
Emerging Technologies Enhancing Blockchain Security
The convergence of blockchain with other cutting-edge technologies promises to revolutionize data security. For instance, advancements in zero-knowledge proofs (ZKPs) allow for verification of data integrity without revealing the underlying data itself, significantly bolstering privacy. Similarly, advancements in homomorphic encryption enable computations on encrypted data without decryption, opening up possibilities for secure data analytics on blockchain platforms. Quantum-resistant cryptography is also crucial, ensuring long-term security against potential attacks from future quantum computers.
These technological advancements will contribute to more robust, efficient, and privacy-preserving blockchain-based security systems.
Scalability and Interoperability Challenges
Despite its inherent strengths, blockchain technology faces scalability limitations. Current blockchain networks struggle to handle the high transaction volumes needed for widespread adoption in data security applications. Solutions such as sharding and layer-2 scaling solutions are being actively developed to address this, but their effectiveness in real-world scenarios remains to be fully tested. Furthermore, the lack of interoperability between different blockchain platforms hinders seamless data exchange and collaboration, limiting the potential for large-scale deployment.
Standardization efforts and the development of interoperability protocols are crucial for overcoming this challenge.
Regulatory Uncertainty and Governance Issues
The regulatory landscape surrounding blockchain technology remains unclear in many jurisdictions. The lack of clear guidelines and regulations creates uncertainty for businesses considering blockchain for data security, hindering widespread adoption. Furthermore, governance models for blockchain networks need to be robust and transparent to ensure accountability and prevent malicious activities. Clear regulatory frameworks and the establishment of effective governance mechanisms are crucial for building trust and encouraging broader adoption.
Predictions for the Future of Blockchain in Data Security
The future of blockchain in data security is bright, but it will be shaped by the successful navigation of these challenges. We can anticipate wider adoption in specific sectors like supply chain management and healthcare, where data integrity and provenance are paramount. The integration of blockchain with other technologies like AI and IoT will create innovative solutions for data security, particularly in areas like identity management and cybersecurity.
However, realizing the full potential will require continued innovation in scalability, interoperability, and regulatory frameworks. For example, within the next five years, we can expect to see a significant increase in the use of blockchain for securing sensitive medical records, driven by the need for improved data privacy and interoperability between healthcare providers. This prediction is based on the current growth in the adoption of blockchain in healthcare pilot projects and the increasing awareness of data security vulnerabilities within the industry.
Illustrative Example: Secure Data Storage using Blockchain
Imagine a healthcare provider, MedSecure, needing to store sensitive patient data while ensuring stringent privacy and security. Traditional methods often fall short, vulnerable to data breaches and unauthorized access. Blockchain technology offers a compelling alternative, creating a transparent, immutable, and highly secure system for managing this crucial information.MedSecure implements a permissioned blockchain network, specifically designed for their internal use and authorized external partners.
This network utilizes a robust cryptographic system to encrypt patient data before it’s stored on the blockchain. Access to this data is meticulously controlled through a sophisticated permissioning model, ensuring only authorized personnel can view or modify specific records. The entire process, from data entry to retrieval, is meticulously logged and auditable, enhancing transparency and accountability.
Data Encryption and Storage
Before any patient data is committed to the blockchain, it undergoes rigorous encryption using advanced algorithms like AES-256. This ensures that even if a data breach were to occur, the encrypted data would remain unintelligible to unauthorized individuals. The encrypted data, along with a unique cryptographic hash, is then stored as a transaction on the blockchain. Each transaction includes a timestamp and a digital signature, verifying its authenticity and preventing tampering.
The blockchain’s inherent immutability guarantees that once data is recorded, it cannot be altered or deleted, providing an unbreakable audit trail.
Access Control and Retrieval
Access to patient data is strictly controlled through a system of digital keys and permissions. Each healthcare professional has a unique digital key, granting them access only to the data they are authorized to view. This granular control prevents unauthorized access and ensures compliance with privacy regulations. When a healthcare professional needs to access a patient’s record, they use their digital key to authenticate their request.
The blockchain network verifies the request and, if authorized, provides access to the encrypted data. The system then decrypts the data using the appropriate key, ensuring only authorized personnel can view the sensitive information. The entire access process is recorded on the blockchain, creating a comprehensive audit log.
Retrieval and Data Integrity Verification
Retrieving data involves the same rigorous authentication and authorization process. Once a legitimate request is verified, the blockchain provides the encrypted data. The authorized user then decrypts the data using their private key. Crucially, the system also provides the cryptographic hash associated with the data. The user can then re-compute the hash of the decrypted data and compare it to the hash retrieved from the blockchain.
A match confirms the data’s integrity, guaranteeing it hasn’t been tampered with since its initial storage. This provides an additional layer of security and ensures the data’s authenticity.
The journey into the world of blockchain in data security reveals a compelling narrative of innovation and resilience. We’ve witnessed how blockchain’s decentralized architecture, cryptographic prowess, and inherent immutability offer a potent antidote to the vulnerabilities of traditional systems. While scalability challenges remain, ongoing advancements and creative implementations are paving the way for wider adoption across various sectors.
The future of data security is undeniably intertwined with the evolution of blockchain technology, promising a more secure and trustworthy digital ecosystem for all.
FAQ Guide
What are the limitations of using blockchain for data security?
While highly secure, blockchain faces challenges like scalability for massive datasets, transaction speed limitations, and the complexity of implementation. The energy consumption of some blockchain networks is also a concern.
How does blockchain compare to traditional encryption methods?
Blockchain enhances traditional encryption by adding a layer of immutability and transparency. While encryption secures data at rest or in transit, blockchain secures the record of that data’s existence and any changes made to it, creating an auditable trail.
Can blockchain prevent all data breaches?
No system is perfectly impenetrable. While blockchain significantly reduces the risk of data breaches by making unauthorized modification extremely difficult, vulnerabilities can still exist in poorly designed or implemented blockchain systems. Human error remains a factor.
Is blockchain suitable for all types of data?
Blockchain is best suited for data requiring high levels of security, transparency, and immutability. It may not be the optimal solution for all data types, especially those requiring frequent updates or high transaction speeds.
What are the regulatory challenges surrounding blockchain in data security?
The regulatory landscape surrounding blockchain is still evolving. Governments are grappling with how to regulate this technology, creating uncertainty for businesses looking to implement blockchain-based data security solutions.
